How to Create an Evacuation Plan for Employees
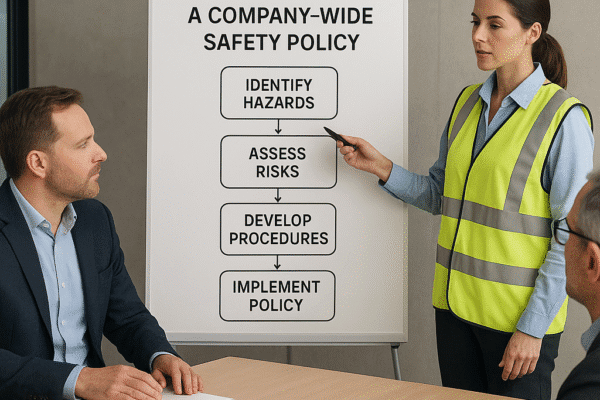
Ensuring a structured response to emergencies is a cornerstone of any robust safety program. A well-crafted evacuation plan not only protects lives but also safeguards organizational assets and reputation. Crafting such a plan involves detailed analysis, clear communication, comprehensive training, and continuous evaluation. The following guide outlines practical steps to develop, implement, and maintain an effective evacuation strategy for employees. Assessing Risks and Identifying Hazards An evacuation plan must begin…